What Is a VPN: How They Work and Why You Might Need One
A VPN is the key to your safety online or away from home.

- VPNs encrypt internet traffic, mask IP addresses and protect data from hackers, ISPs and governments, enhancing online privacy and security.
- VPNs are essential for bypassing geo-restrictions, securing public Wi-Fi usage, enabling remote work access and protecting sensitive personal data.
- Look for VPNs with multiple simultaneous connections, a no-log policy, extensive server networks, cross-platform compatibility and features like kill switches and SmartDNS.
For those unfamiliar, a Virtual Private Network (VPN) allows you to browse the web, access resources and communicate privately and securely as if you were directly connected to a private network. If you’ve never used a VPN before or are only vaguely familiar with what they are, how they work and what the benefits are, it can feel a bit intimidating. We’re here to explain everything you need to know about VPNs so you can decide how they might benefit you online.
Our Video on VPNs
Don’t have time to read the entire article? Watch our video below and subscribe to our YouTube channel for more helpful guides and explainers on all things internet.
Overview of VPNs
- What’s a VPN?
- How Does a VPN Work?
- When to Use a VPN
- The Features of a VPN
- Types of VPN COnnections
- Top VPN Companies
- Privacy Considerations for Using a VPN
What’s a VPN?
A VPN is software or hardware that disguises or masks your internet service, making it appear as though it’s originating from somewhere else. It creates a private network that extends across a public network infrastructure, allowing you to securely transmit data as if your devices were directly connected to a private network. Without a VPN, websites, hackers and the government have easy access to your internet traffic data.
When you visit a website from your home internet connection, you’re providing that website with an IP Address, which is a bit like providing your street address. When you visit a website through a VPN, you’re providing the VPN “street” address to the website instead. When you connect to a VPN server, your internet traffic is routed through an encrypted tunnel, protecting it from interception or monitoring by hackers, governments or internet service providers (ISPs). This encryption ensures that even if someone were to intercept the data, they would only see encrypted gibberish without the decryption key.
How Does a VPN Work?
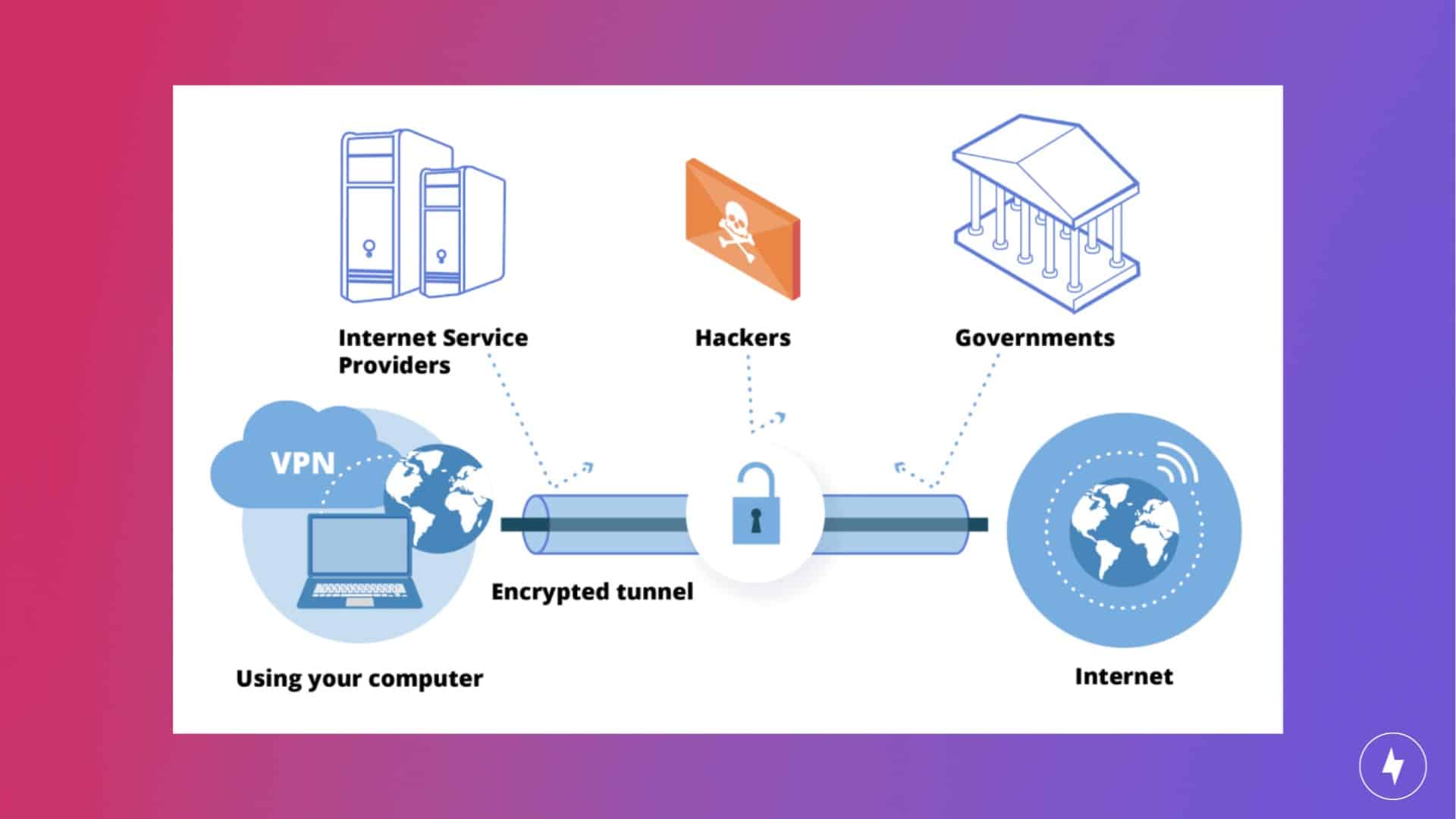
Your Internet Protocol (IP) address is a numerical designator assigned to any device using the Internet Protocol for communication, such as a phone, tablet or laptop. IP addresses can be used to find an internet user’s ISP, internet traffic data or physical location.
A VPN encrypts user data and disguises location by use of multiple servers. The VPN server acts as an intermediary between your device and the internet, masking your actual IP address and replacing it with the IP address of the VPN server. This process effectively anonymizes your online activities and hides your true location from websites, ISPs and other third parties. Instead of a would-be hacker finding your IP while you surf the web in California, they will find the IP address of your VPN service in Germany, Canada, Sweden or wherever the VPN provider has servers.
When you initiate a connection to a VPN server, your device encrypts all outgoing data packets before sending them through the internet. This encryption process ensures that even if intercepted, the data remains unreadable to unauthorized parties. The encrypted data packets are then transmitted through the internet to the VPN server, where they are decrypted and forwarded to their intended destination, whether it’s a website, application or another service.
When to Use a VPN
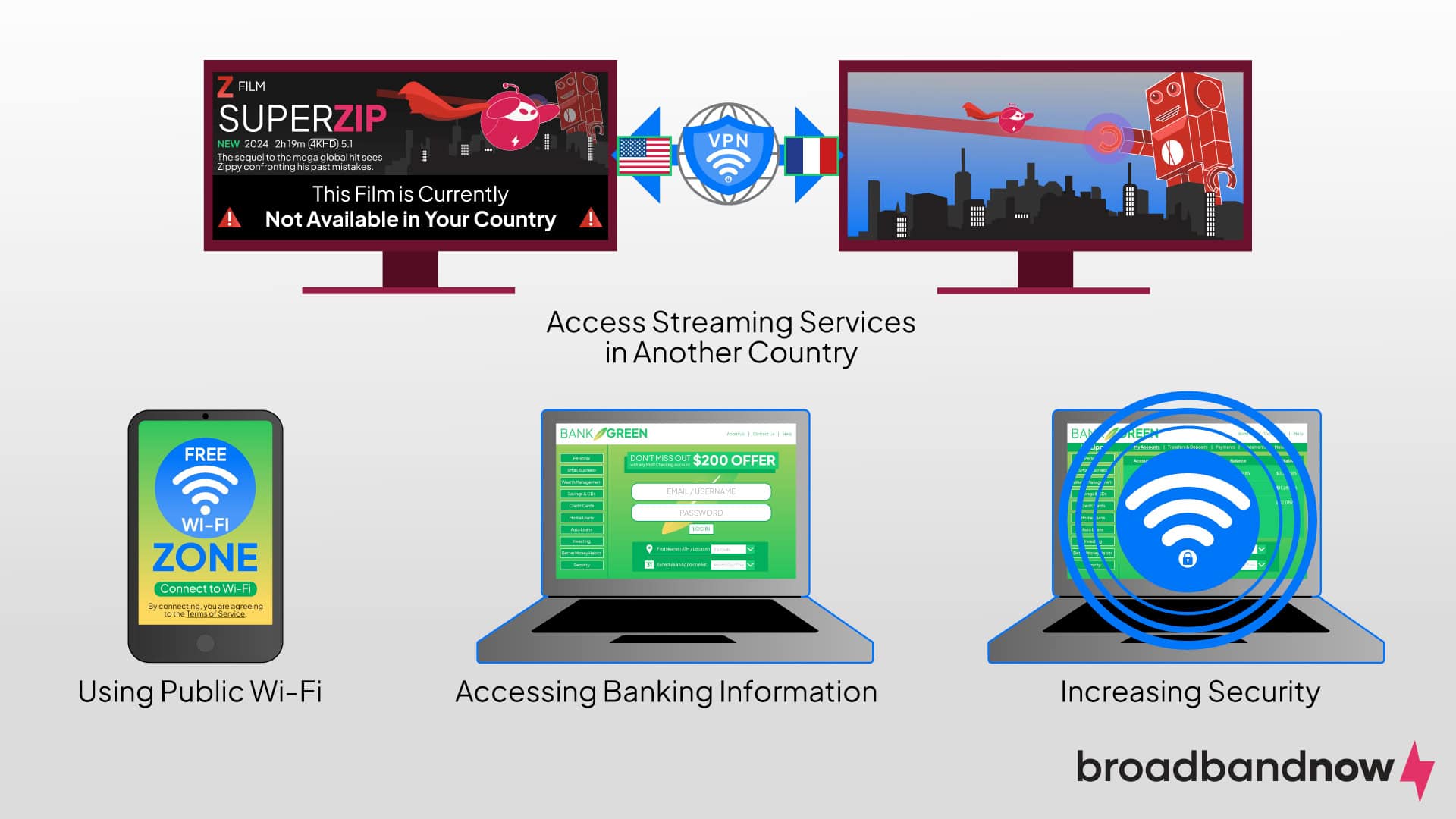
VPNs are used for many reasons. Traveling to the vast reaches of the internet without protection can leave you open to malware attacks, identity theft and ransomware. A VPN creates a buffer between you and the internet. Because VPNs encrypt data, your internet traffic will be inaccessible to your ISP, mobile carrier or anyone else trying to acquire your information.
You might want to use a VPN if you are trying to do any of the following:
- Access websites blocked in your region
- Securely browse sensitive personal data
- Download torrents and other media
- Access cheaper prices for certain goods
- Access remote work platforms
- Increase your security and sense of privacy online in general
- Use unsecured public Wi-Fi
Many people use VPNs while traveling because connecting to public Wi-Fi can leave internet users vulnerable. They can also log into their office’s network when working remotely. If you’ve traveled to a country that bans Google, Twitter or YouTube, you can use a VPN to connect to a server located in a country where those sites aren’t prohibited.
You might not realize that streaming services offer different TV shows and movies depending on where you are in the world. Do you live in the U.S. but would like to see what Netflix has available in France? Use a VPN.
There aren’t many downsides to using a VPN, as the good outweighs the bad. Some websites don’t allow VPN users, but there are volumes written online about how to circumvent VPN blockers. Using a VPN will cause your connection to be slower, but checking a VPN’s speed is easy. Most of the time, slow speeds can be remedied by connecting to a server located closer to your location.
Pros of Using VPNs
- Enhanced privacy
- Bypassing geo-restrictions
- Secure remote access
- Anonymous browsing
- Secure public Wi-Fi
- Avoiding internet censorship
Cons of Using VPNs
- Decreased speed
- Service can be costly
- Requires trust in a VPN provider
- Potential for connection drops
The Features of a VPN
All VPN products offer the basic functionality of masking your home connection, but several features are more specific, yet equally important.
- Simultaneous connections: Today, consumers have an average of 17 connected devices in their homes. Having a VPN that allows you to use multiple devices at the same time under your virtual network is critical. Thankfully, most quality VPN services offer this feature, but some don’t offer protection for as many devices as others. So it’s important to pay close attention to this before signing up.
- Transparent logging: VPNs handle the “logging” of your online activities in different ways. Some of them can store certain elements of your browsing history for a period of time. Ideally, you want to find a service that offers a “no-log” policy, as these will be the most private. However, read the terms carefully: Some providers will claim that they do not log while still collecting certain scraps of data, such as session logs that might reveal your activities.
- Large number of servers: When you connect to a VPN, your personal connection is communicating with a server in a secondary location. In an ideal situation, this server will be as close as possible to your home so your network performance doesn’t suffer too drastically. A VPN with a large number of servers is more likely to have a server or two near you.
- Cross-platform functionality: We recommend choosing a VPN that offers dedicated PC and Mac applications as well as Android and iOS versions. This way, you can ensure you’re getting the most bang for your buck when committing to one service.
- Integrated network kill switch: No matter how solid your VPN is, no service is perfect. There will be times when your virtual connection fails, which can lead to your actual network (and associated IP address) being “leaked out.” This is especially common when your preferred service is under heavy load. Ensure that your VPN has an integrated kill switch. This is an emergency function that will automatically “kill” the connection, preventing data from being transferred.
- SmartDNS support: SmartDNS functionality allows you to access one of the most useful features of a VPN — the ability to bypass “geo-blocked” content restrictions — without sacrificing speed due to connecting to a virtual network. Some devices do not allow a VPN to be directly installed. If your VPN supports SmartDNS, you can still use it in conjunction with your regular network to bypass content restrictions in this case.
Types of VPN Connections

Not all VPN connections are created equal. There are various types, each serving specific purposes and requirements. Understanding the distinctions between these VPN types is crucial for selecting the most suitable option based on individual or organizational needs.
- Remote Access VPN: Enables you to securely connect to a private network from a remote location, commonly used by employees working from home or traveling.
- Site-to-Site VPN: Establishes secure communication between entire networks, such as branch offices or data centers, allowing them to communicate as if directly connected.
- Peer-to-Peer VPN (P2P VPN or Overlay VPN): Facilitates direct communication between individual devices without the need for a central server, often used for decentralized and privacy-conscious purposes like file sharing or collaborative work.
Top VPN Companies
There are many VPN companies online to choose from, and because security is a top concern for VPN usage, you can’t just choose one without proper research. We’ve rounded up some of the top choices below, but you’ll want to spend a great deal of time researching which one you choose to ensure it meets your safe browsing needs.
Proton VPN
There are plenty of free VPN services available online, but few are as safe or comprehensive as Proton VPN. Most free VPN services aren’t trustworthy, but Proton VPN is the exception. Proton VPN allows you to establish 10 simultaneous VPN connections and access over 500 servers. The service also provides advanced privacy tools and has a strong stance on customer privacy. The easy-to-navigate interface is another way the company delivers a quality VPN service.
Some drawbacks to Proton VPN’s service include challenges implementing it on ChromeOS and limited customer support availability. If you’re looking for more features in a VPN, including email, calendars and a document drive, you can upgrade to Proton VPN’s premium plans.
NordVPN

NordVPN stands out as one of the best VPN services online. Noteworthy features include the ability to establish up to six simultaneous VPN connections and access to a vast network of over 500 servers. NordVPN users praise its excellent user interface and appreciate the inclusion of built-in antivirus tools, as well as features for traffic routing and file sharing.
One of the main criticisms of NordVPN’s service is its limitations in malware-blocking capabilities. The service is also relatively expensive compared to other options. NordVPN offers subscription plans with discounts available if you commit to one-year or two-year terms.
ExpressVPN

ExpressVPN is another popular VPN service praised for its strong security practices and stylish interface. These features make the service appealing if you seek both functionality and aesthetics. On ExpressVPN, you can establish up to five simultaneous VPN connections and access a network of over 500 servers. The service also offers split tunneling functionality for enhanced control over internet traffic.
ExpressVPN lacks the ability for multi-hop connections, which may be a downside for users with specific privacy needs. Similar to NordVPN, ExpressVPN is a bit on the pricey side. However, it offers subscription options, with discounts available for those opting for six-month or one-year plans.
Privacy Considerations for Using a VPN
Ensuring a private connection is of the utmost importance when using a VPN. You need to be aware of what privacy considerations to look out for as you search for a VPN servicer.
What Is Encryption?
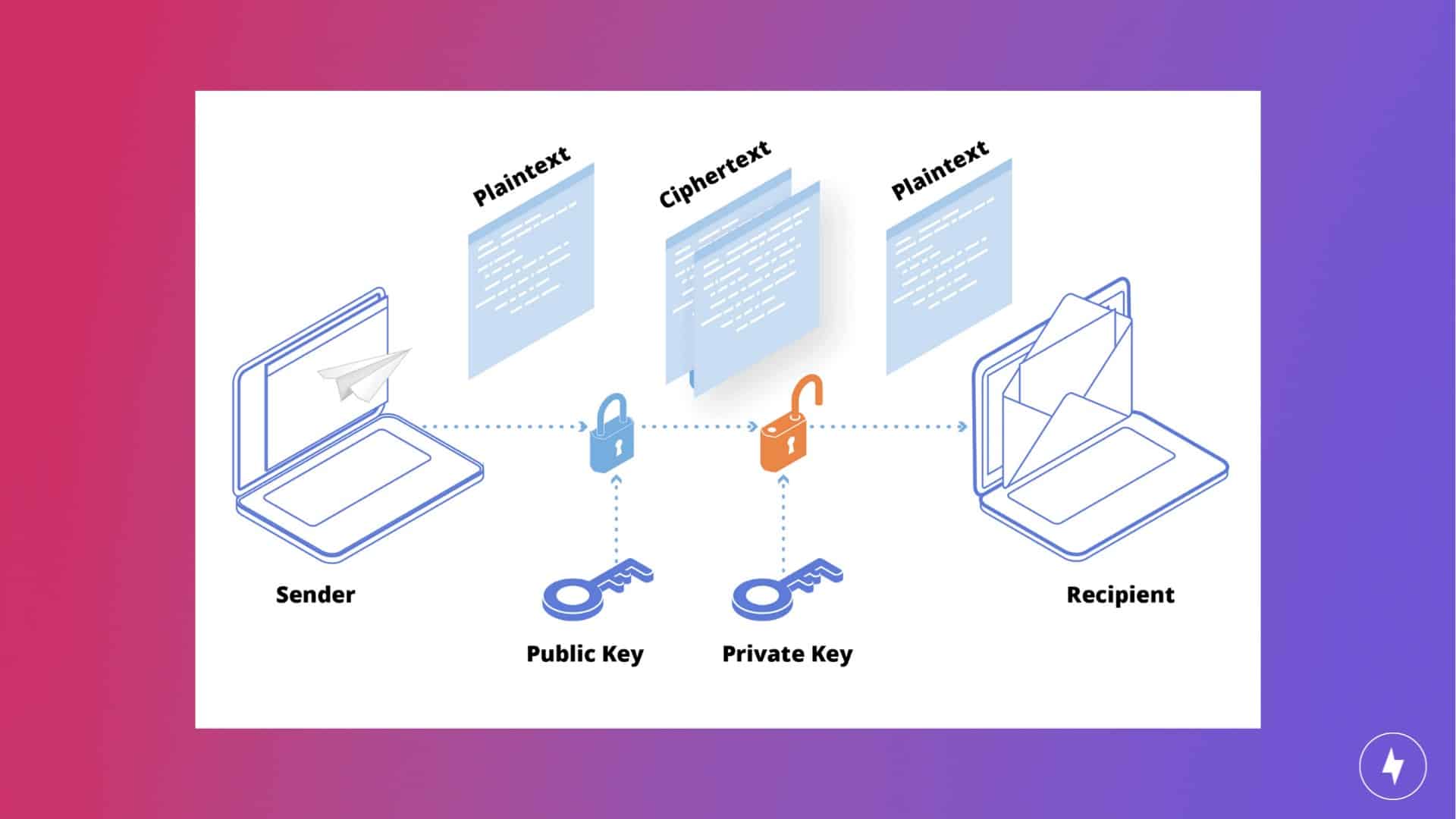
Put simply, encryption is the process of making sensitive data indiscernible to anyone outside of a secure environment. Data is commonly converted into ciphertext — random strings of characters that are meaningless on their own — before being sent across the internet at large. When it arrives at its destination, a unique “key” is used to translate the ciphertext back into something intelligible.
Encryption is an entire ocean of a topic and one that’s well above the scope of this guide. What you should know, for the purposes of buying the best VPN, is that it’s generally accepted that AES-256 encryption is the most robust on offer currently. It’s the only standard to be officially endorsed by the National Security Agency (NSA) and is virtually unbreakable by today’s standards.
What Are 5 Eyes, 9 Eyes and 14 Eyes Alliances?

Starting around the time of the Cold War, an alliance today known as 5 Eyes sprouted from an intelligence pact called the UKUSA Agreement. Originally an intel-sharing agreement between the U.K. and the U.S., the two superpowers were shortly joined by New Zealand, Canada and Australia.
In the early 2000s, the existence of at least two more global intelligence-sharing agreements was disclosed. Commonly referred to as 9 Eyes and 14 Eyes, these include even more countries across the globe, each with varying levels of involvement and organization. Above is a visual breakdown showcasing each member state.
These alliances primarily focus on intelligence sharing and cooperation in signals intelligence (SIGINT) activities, which involve monitoring and intercepting communication signals like emails, phone calls and internet traffic. The awareness of international surveillance alliances and their potential privacy implications can underscore the importance of using VPNs as a tool to safeguard online privacy and security.
Company History and Location: Before hopping on board, it’s a good idea to research the parent company behind a given VPN. It’s also important to consider where a company is located (as in, whether it is in a 5, 9 or 14 Eyes country). The world of cybersecurity is marked by constant change, so check in now and then and ensure everything is above board.
Are VPNs Legal?
Yes, VPNs are legal, but not everywhere. The odds are great that you’re reading this from a country where VPNs are perfectly legal. Some countries, however, such as Russia, North Korea, Egypt, Iran, the United Arab Emirates and China have banned or tightly regulated the use of VPNs.
Despite their illegality in some countries, no one has ever been arrested and prosecuted for using a VPN. What you do with the VPN in those countries gets you in trouble.
Are Free VPN Services Safe?
If you do some searching, you’ll likely come across several VPN services that claim to be 100 percent free. Unfortunately, the vast majority of these services can’t be trusted. Proton VPN is generally considered one of the only reputable free VPN services. If you’re determined to go with a free option, we recommend that you read through the privacy and data sections carefully. If there isn’t one, consider this a massive red flag, and sign up at your own risk.
Frequently Asked Questions About a VPN
Do I need a password manager if I have a VPN?
For comprehensive online security, it’s highly recommended that you use a password manager like Keeper alongside a VPN. A password manager stores and encrypts passwords, generates strong and unique passwords for each account and automates login processes, reducing the risk of password-related vulnerabilities such as reuse or weak passwords.
Who can see if I use a VPN?
While your ISP and network administrators can see that you’re connected to a VPN and the amount of data being transmitted, they can’t decipher the encrypted traffic or monitor the specific websites you visit or the content you access. The VPN provider itself may have access to your internet traffic, which is why it’s crucial to choose a reputable provider that upholds strict privacy policies and does not log user activity.
Are there any alternatives to VPNs?
Proxies reroute traffic to conceal IP addresses without encryption, offering anonymity but risking data security, especially on free networks. SSH tunnels and Software-Defined WANs (SD-WANs) provide secure alternatives, with the former encrypting traffic through port forwarding and the latter optimizing bandwidth and centralizing management for businesses. Secure Access Service Edge (SASE) integrates SD-WAN, zero-trust access and other security features into a unified cloud solution, enabling secure, efficient remote access to both on-premises and cloud assets.
How long can I leave my VPN on?
You can leave your VPN on for as long as you need continuous protection and privacy while browsing the internet. There’s no specific time limit for how long a VPN can remain active, as it largely depends on your usage patterns and preferences. Many people choose to keep their VPNs running constantly, especially when connected to unsecured or public Wi-Fi networks, to ensure continuous encryption of their internet traffic and protection against potential threats.
Is VPN safe for online banking?
Using a VPN for online banking can enhance security and privacy to reduce the risk of unauthorized access to your financial information. VPNs create a secure and encrypted connection between your device and the banking website, making it more difficult for hackers or malicious actors to intercept sensitive data such as login credentials, account numbers and financial transactions.